Security
The comprehensive NLS security module is accessed from the Security slider on the shortcut bar or from the View > Security menu.
The comprehensive NLS security module is accessed by clicking  Security on the shortcut bar and selecting
Security on the shortcut bar and selecting  User or
User or  Group then the
Group then the  Privileges tab or by selecting
Privileges tab or by selecting  Default Privileges to configure the default settings that may be applied to all new users or groups.
Default Privileges to configure the default settings that may be applied to all new users or groups.
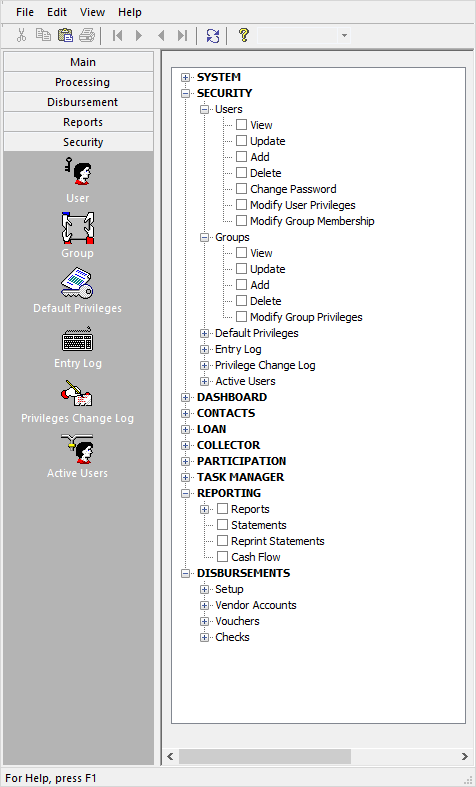
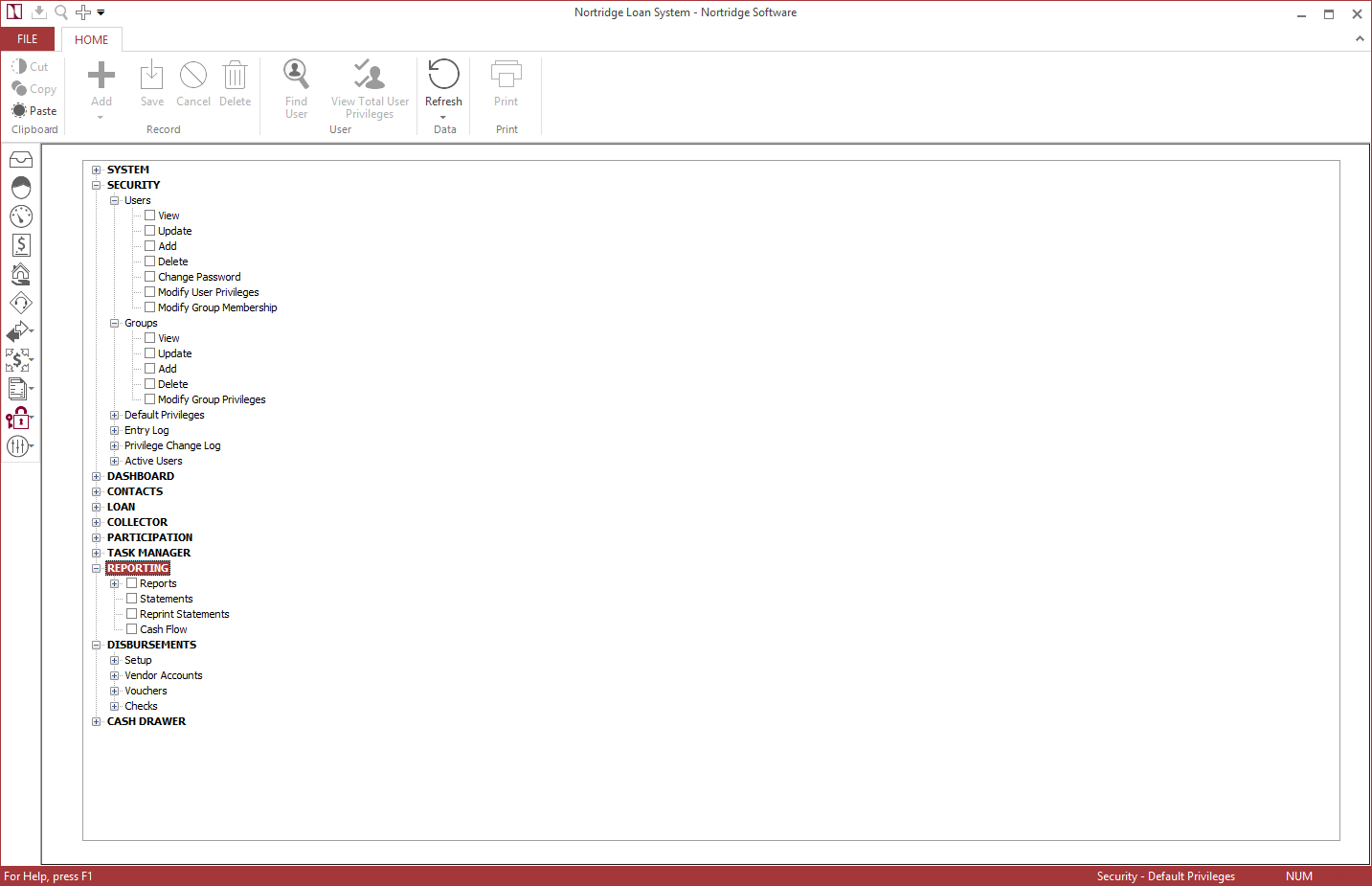
NLS security is built around a privilege tree that is used to assign privileges. This tree allows the system administrator to set up privileges for individual users, groups of users, or system defaults. Every function in NLS has its own set of privileges. A user will have access to any functions for which a privilege has been granted in personal privileges, in the group privileges as a member of the group, or any privileges specified in a trustee access. The user only needs to have a specific privilege in one place to be able to access a specific function.
The privilege tree is a hierarchy in that if a certain privilege is granted at the parent level, then that privilege will also be granted to all of its children. So if Loan > Loan Records > Update privilege is granted, the Update privilege (where applicable) for all of the fields under Loan > Loan Records > Field Level Access will be granted (regardless of whether the Update privilege for each individual field is granted or not). Conversely, if Loan > Loan Records > Update privilege is not granted then the Update privilege for each field under Loan > Loan Records > Field Level Access must be selected individually to grant Update privilege to those fields. This applies to all privileges (View, Update, Add…) in all categories that are common between the parent and its children.
Note
Trustee access can be configured in the following areas of Setup: comment category, contact type, collateral, loan group, loan portfolio, status codes, transaction codes, and task template.Trustee access can also be configured on a per loan, per contact, or per campaign* basis by querying a loan, contact, or campaign and selecting File > Trustee.
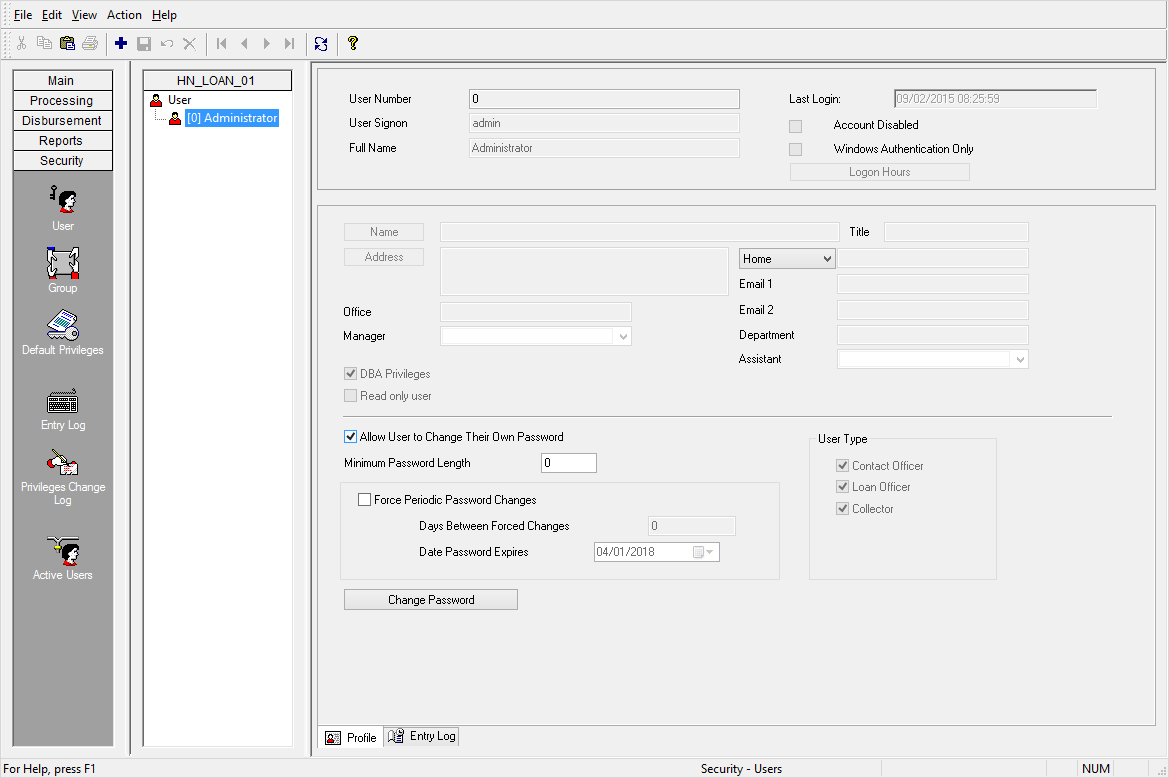
The user account contains the user’s profile, individual privileges, group membership, entry log, and privileges change log. The profile contains the user’s system password and password expiration information, and the logs allow the system administrator to track the user’s access to the system.